Summary
- Cybersecurity in industrial space is critical, as Operational Technology (OT) and Industrial Control Systems (ICS) are increasingly targeted.
- Threats are sophisticated, including ransomware in manufacturing, supply chain attacks, and sophisticated nation-state actors.
- The primary risk stems from the convergence of OT vs IT security and the security gaps in legacy systems.
- Effective solutions include robust network segmentation, continuous threat detection, asset visibility, and a strong culture of personnel training.
- Securing industrial control system security requires specialized tools that understand OT protocols and the operational context of the plant floor.
Introduction
The factory floor, once protected by a physical “air gap,” is now a digital frontier. With the rapid expansion of the Industrial Internet of Things (IIoT) and the drive for operational efficiency, cybersecurity in industrial space has moved from an IT concern to a core business imperative. Modern manufacturing facilities, utilities, and critical infrastructure rely on complex networks of Operational Technology (OT) and Industrial Control Systems (ICS) to manage everything from turbine speed to assembly line robotics. This digital transformation, while hugely beneficial, exposes these systems to crippling cyber risks.
The statistics are stark: According to IBM’s Cost of a Data Breach Report (2024), the average cost of a data breach in the industrial sector, including manufacturing and energy, is among the highest across all industries. This highlights the severe financial and physical consequences of a breach in this environment. When an attack hits an industrial plant, it can lead to physical damage, environmental hazards, costly downtime, and even loss of life.
The challenge is unique. Unlike Information Technology (IT), where the focus is confidentiality, the OT world prioritizes availability and safety above all else. This difference demands a specialized approach.
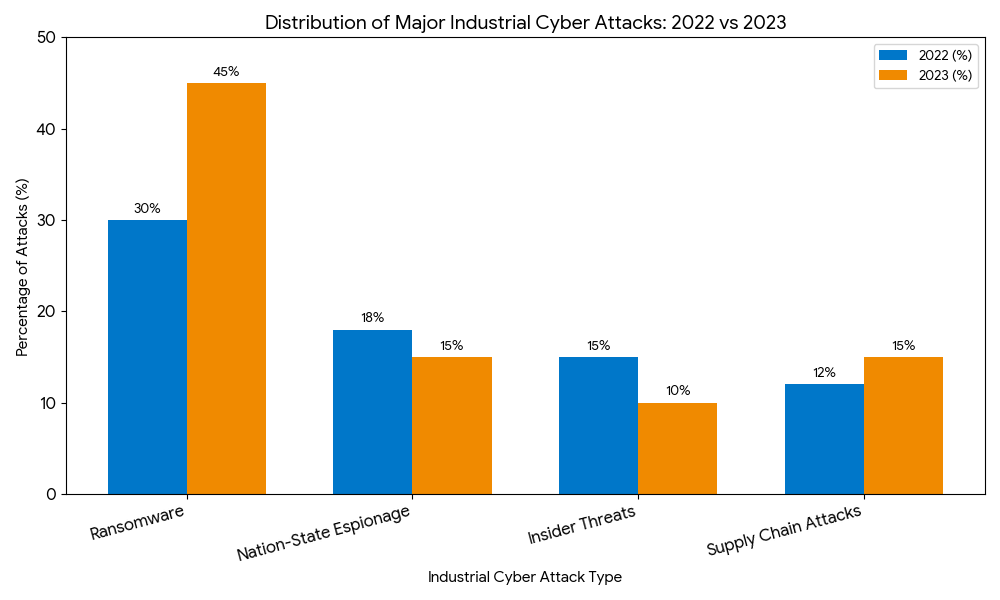
What Are the Most Common Types of Industrial Cyber Threats?
The threat landscape for OT environments is a volatile mix of motivated cybercriminals, sophisticated nation-state actors, and even unintentional internal errors. Understanding these risks is the first step toward building a robust OT security posture.
The Dominance of Ransomware and Destructive Malware
The most prominent threat facing the industrial control system security space today is ransomware. Attack groups view manufacturers and utilities as high-value, high-pressure targets. Operations Managers and Plant Directors are often under intense pressure to restore production quickly, making them more likely to pay a large ransom demand.
In manufacturing, an attack can freeze Supervisory Control and Data Acquisition SCADA cybersecurity systems, halt production lines, and lock out operators. Malware, such as that seen in the infamous Stuxnet attack, is specifically engineered to target and manipulate ICS components like PLCs (Programmable Logic Controllers), causing physical damage without simply encrypting files.
Attacks on the Supply Chain and Third-Party Risk
In today’s interconnected economy, an organization’s weakness is often found in its partners. Supply chain attacks involve compromising a trusted vendor (like an automation software supplier or an equipment manufacturer) to gain access to the main target’s network.
This vector is particularly dangerous for industrial plants because new equipment is often installed with factory-default passwords and potentially vulnerable, unpatched firmware. This is a critical area for critical infrastructure cybersecurity, where vendors must adhere to strict security requirements before they can connect to the plant network. How many organizations truly audit their vendors’ remote access points before allowing a connection?
The Threat from Industrial IoT Devices
The deployment of sensors, smart meters, and industrial IoT (IIoT) devices has created an enormous new attack surface. These small, often low-cost devices are typically deployed without strong native security, making them an ideal entry point for adversaries. They often operate on unmanaged, flat networks, allowing an attacker to quickly pivot from a compromised IIoT device to a mission-critical PLC. Securing these endpoints is a growing challenge for industrial network security.
Modern Solutions for Robust OT & ICS Safety
Securing the modern industrial environment requires a fundamental shift in strategy. It moves away from the traditional IT ‘castle-and-moat’ defense toward a zero-trust model that understands the unique characteristics of OT systems.
Achieving Comprehensive Asset Inventory and Visibility
You can’t protect what you don’t know exists. For many legacy plants, a complete, accurate inventory of all connected devices, including PLCs, RTUs, HMI workstations, and even decades-old servers, simply doesn’t exist.
A foundational step in modern industrial cybersecurity is continuous, passive monitoring to discover every asset. This process must map network communications and identify vulnerabilities without disrupting sensitive control processes. The technology employed for this should specialize in recognizing native industrial automation security protocols like Modbus, DNP3, and EtherNet/IP, providing a clear map of the control process.
- Passive Monitoring: Using non-intrusive network taps (TAPs) or SPAN ports to collect data without injecting traffic.
- Protocol Analysis: Deep packet inspection (DPI) to understand the commands being sent, not just the network traffic.
Network Segmentation and Zero Trust Architecture
The old model of having a single firewall between the IT and OT networks (the OT vs IT security boundary) is no longer sufficient. Modern best practice advocates for deep, micro-segmentation within the OT environment itself, isolating critical system components.
This is where a Zero Trust Architecture (ZTA) comes into play. In an OT context, ZTA means:
- Never trust, always verify: Every device and user, regardless of location, must be authenticated and authorized.
- Least Privilege: An engineer’s workstation should only be able to communicate with the specific PLCs it needs to manage, and for no other reason.
- Use Firewalls & Data Diodes: Deploy industrial firewalls at critical junction points and, where appropriate for high-security unidirectional data flow, consider using data diodes.
Industrial Cyber Threat Intelligence
Knowledge is power, especially when facing highly adaptable threats. Industrial cyber threat intelligence is the collection, analysis, and dissemination of information about threats, vulnerabilities, and adversaries that specifically target ICS/SCADA environments. This data allows organizations to shift from a reactive to a proactive defense posture.
Why is it important? Because it provides context. If a new vulnerability is being actively exploited in similar water utility systems globally, specialized intelligence will flag that specific risk before a generic IT feed would, allowing the plant to patch or create a temporary mitigation plan immediately.
Best Practices and the Human Element in Industrial Security
While technology provides the tools, people and processes are what make a security program effective. Establishing clear, enforceable best practices is essential for sustained safety.
Patch Management and Legacy System Security
Patching is difficult in OT. Systems often run 24/7, and many legacy systems (some running Windows NT or older proprietary OS) cannot be patched without significant downtime or vendor approval. For these reasons, security strategies must emphasize compensating controls:
- Virtual Patching: Using an intrusion prevention system (IPS) to block exploit attempts targeting known vulnerabilities in unpatched software.
- Application Whitelisting: Preventing all unauthorized software from executing on critical HMI and engineering workstations. If a system only needs to run the SCADA application, only that application is allowed to execute.
Securing Access and Remote Connections
Remote access is a major vulnerability, especially for vendors performing remote diagnostics or updates. Best practices demand that any external connection:
- Use a Multi-Factor Authentication (MFA) enabled Virtual Private Network (VPN).
- Be logged, monitored, and time-bound.
- Be overseen and approved by an internal Plant Manager or OT Manager before activation.
For an Industrial Automation Engineer or a Maintenance & Reliability Engineer, this can feel like an unnecessary hurdle, but it is a non-negotiable step to protect operations from external intrusion.
Continuous Training and Incident Response
Humans are the first and often the last line of defense. A security-aware culture can spot phishing attempts and follow protocol. Training shouldn’t just focus on IT staff but must be tailored for Plant Managers, operators, and field technicians, focusing on the operational impact of their actions.
A well-drilled industrial cyber attack prevention plan is also crucial. The plan must detail specific, OT-aware steps, such as safely shutting down or isolating sections of the plant (a “safe-state” mode) if a compromise is detected. This minimizes physical damage and contains the threat, allowing the organization to execute a thorough forensic investigation and recovery. This rigorous preparation is a hallmark of strong cybersecurity for manufacturing.
Conclusion
The convergence of IT and OT has permanently changed the risk profile of industrial operations. The challenge of cybersecurity in industrial space requires specialized knowledge; you can’t secure a PLC with the same tools you use to secure an email server. By prioritizing asset visibility, implementing robust network segmentation, embracing zero-trust principles, and investing in continuous personnel training, organizations can build the resilience needed to face sophisticated adversaries. Protecting your physical assets and ensuring operational continuity is not a technology problem; it’s a business one that demands immediate executive attention and investment.
Frequently Asked Questions (FAQ)
-
What are the most common types of industrial cyber threats?
The most common threats targeting industrial environments, specifically Operational Technology (OT) and Industrial Control Systems (ICS), are highly financially motivated. Ransomware in manufacturing and utilities is currently the most dominant threat, designed to halt production and force a quick payout. Other significant threats include destructive malware targeting PLCs (like Stuxnet variants), nation-state actors seeking espionage or sabotage, and supply chain compromises that exploit vulnerabilities in trusted vendor software or hardware.
-
What are the best cybersecurity practices for industrial systems?
The best practices center on protection and resilience. This starts with a complete and accurate asset inventory and network mapping. The technical pillars are network segmentation (using the Purdue Model as a guide) to isolate critical Level 1 and 2 control systems, and implementing Zero Trust principles for all access. Operationally, organizations should enforce strict remote access policies using Multi-Factor Authentication (MFA) and implement continuous, passive ICS threat detection that understands industrial protocols.
-
How can organizations effectively secure OT networks?
Securing OT networks effectively requires tools designed for the OT environment. Crucially, this means using passive monitoring technology that doesn't inject traffic and risk disruption. Security architecture should prioritize the air-gapping of IT and OT, or at minimum, use industrial firewalls and data diodes for secure data flow. Furthermore, a strong patch management strategy and the use of application whitelisting on all HMI and engineering workstations are key compensating controls for unpatchable, legacy equipment.
-
What cyber attacks are most common in manufacturing?
Manufacturing is heavily targeted by financially motivated cybercriminals, making ransomware the most common type of attack. These attacks aim to disrupt the production line, causing costly downtime and operational losses. Other common attacks include intellectual property theft (espionage) via compromised engineering workstations, and attacks leveraging vulnerabilities in Industrial IoT (IIoT) devices connected to the manufacturing network to gain an initial foothold.
-
What cybersecurity risks do industrial plants face?
Industrial plants face unique risks that extend beyond typical data breaches. The primary risks are physical safety and operational downtime. A successful attack can lead to the manipulation of physical processes (e.g., over-pressurizing a vessel), causing equipment damage or safety hazards. The risk of prolonged operational downtime due to ransomware or a debilitating malware infection means significant financial losses and reputational damage. The use of legacy systems and the security gap created by OT vs IT security convergence also pose continuous, systemic risks.



